Kerberos, Tickets Tokens And Authentication An Introduction To Kerberos Appway Community
Kerberos provides secure authentication for various services at Stanford such as Stanford OpenAFS. Protocols and file formats.
Kerberos I How Does Kerberos Work Theory
Kerberos is a well-known and widely used authentication protocol that also lies at the heart of Microsofts Active Directory.
Kerberos. Kerberos uses cryptographic tickets to avoid transmitting plain text passwords. It is designed at MIT to allow network resources in a secure manner. Kerberos was discovered on June 28 2011 by a large team led by Mark Showalter using the Hubble Space Telescope.
Kerberos is a computer network security protocol that authenticates service requests between two or more trusted hosts across an untrusted network like the internet. A free implementation of this protocol is available from the Massachusetts Institute of Technology. The main components of Kerberos are.
Given this stature it has become one of the protocols most targeted for abuse by adversaries of all shades. How to build this documentation from the source. Contributing to the MIT Kerberos Documentation.
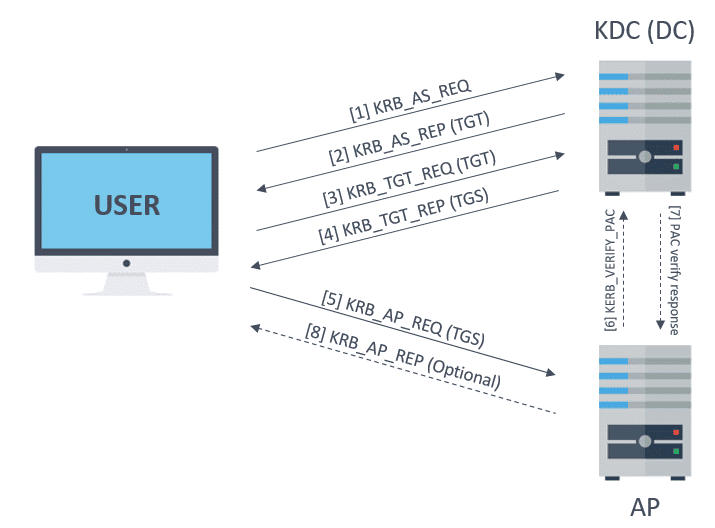
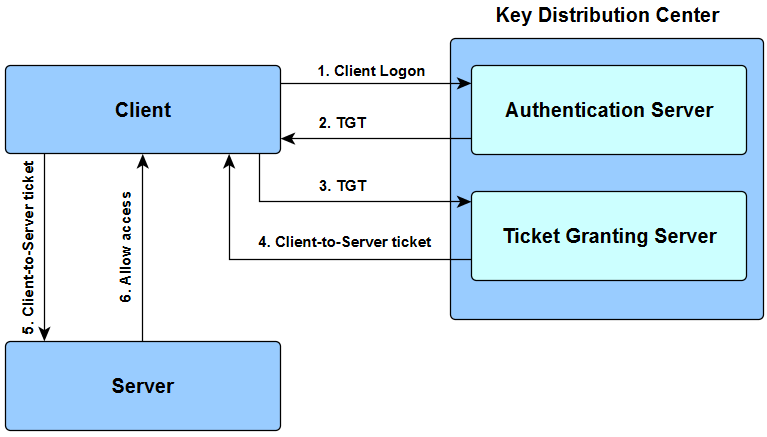
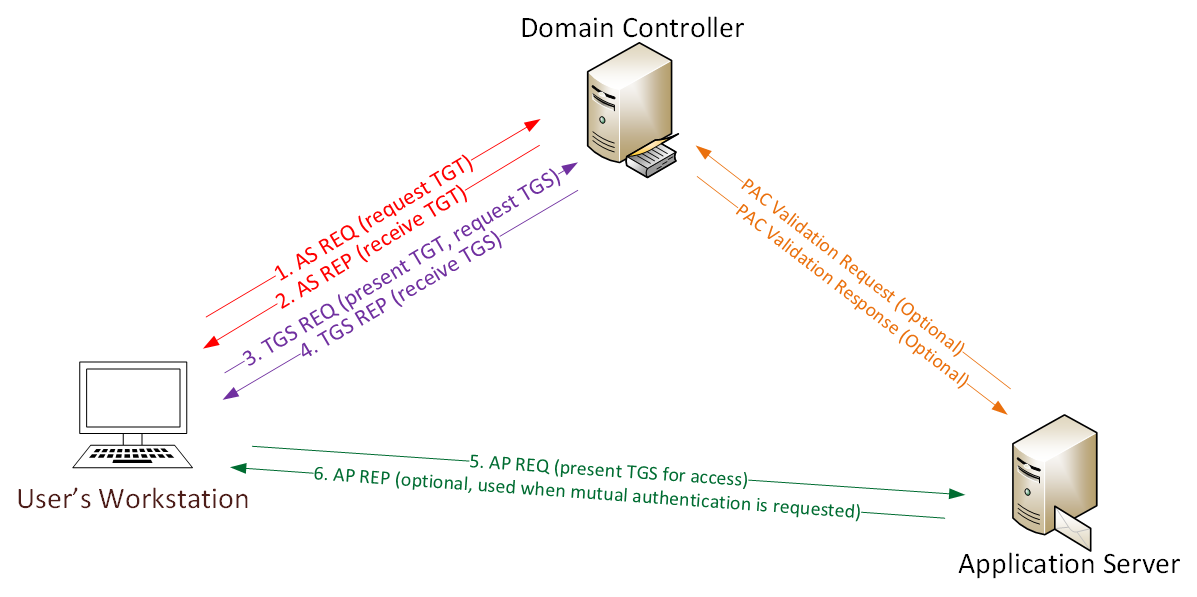
KfW is a software application that installs tickets on a computer in order to grant access to essential MIT services. For Windows a utility called Network Identity Manager provides the graphical user interface for managing Kerberos functions. Kerberos runs as a third-party trusted server known as the Key Distribution Center KDC.
Kerberos Dante a character from Saint Seiya. The application provides customizations for some MIT applications requiring Kerberos authentication enabling you to gain secure access to SAPgui and connect to Athena via SSH. Kerberos moon a moon of Pluto.
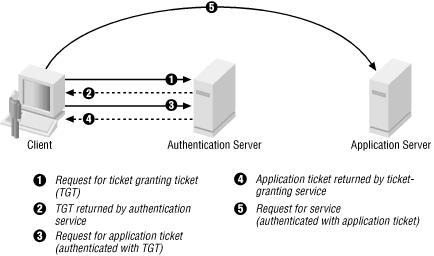
The Authentication Server performs the initial authentication and ticket for Ticket Granting Service. For plugin module developers. MIT Kerberos for Windows KfW is an integrated Kerberos release for Microsoft Windows operating systems.
It is designed to provide strong authentication for clientserver applications by using secret-key cryptography. Each user and service on the network is a principal. Kerberos is available in many commercial products as well.
It is designed at MIT to allow network resources in a secure manner. With SSO you prove your identity once to Kerberos and then Kerberos passes your TGT to other services or machines as proof of your identity. Kerberos is adopted by a huge number of industries so any new weaknesses in its security protocol or in underlying modules are quickly corrected.
The weakest link in the Kerberos chain is the password. Both client and server can also be. Kerberos is a network authentication protocol.
Kerberos is built in to all major operating systems including. Kerberos is a protocol for authenticating service requests between trusted hosts across an untrusted network such as the internet. The installer installs the 32-bit version on 32-bit Windows operating systems and the 64-bit version on 64-bit Windows.
If a non-authorized user has access to the Key Distribution Center the whole authentication system is compromised. The weaknesses of Kerberos are. A free implementation of this protocol is available from the Massachusetts Institute of Technology.
Kerberos mythology or Cerberus the hound of Hades. There is a chance it appeared as a very faint smudge in. It was confirmed in subsequent Hubble pictures taken on July 3 and July 18.
Using Kerberos authentication within a domain or in a forest allows the user or service access to resources permitted by administrators without multiple requests for credentials. Kerberos authentication supports a delegation mechanism that enables a service to act on behalf of its client when connecting to other services. Kerberos Productions a game development studio.
The moon was not seen in earlier Hubble images because the exposure times were shorter. Kerberos shares a secret key with the KDC. Kerberos is a network authentication protocol.
The Kerberos authentication protocol provides a mechanism for mutual authentication between entities before a secure network connection is established. So when it comes to Computer Science. It uses secret-key cryptography and a trusted third party for authenticating client-server applications and verifying users identities.
Throughout this documentation the two entities are called the client and the server even though secure network connections can be made between servers. In this article we will see discussed the Kerberos concept and its working with the help of an example. Kerberos excels at Single-Sign-On SSO which makes it much more usable in a modern internet based and connected workplace.
This secret key is known only to the KDC and the service principal on each IBM Streams resource. It is designed to provide strong authentication for clientserver applications by using secret-key cryptography. According to Greek mythology Kerberos Cerberus was the gigantic three-headed dog that guards the gates of the underworld to prevent the dead from leaving.
Kerberos protocol a computer network authentication protocol to. Kerberos is a computer network authentication protocol. Kerberos may refer to.
User principals obtain ticket-granting tickets from the Kerberos KDC and present those tickets as their network credentials to gain access to IBM Streams services and interfaces.
Configuring Kerberos Authentication Protocol Datasunrise Data Db Security
Detecting Forged Kerberos Ticket Golden Ticket Silver Ticket Use In Active Directory Active Directory Security

How Kerberos Authentication Works
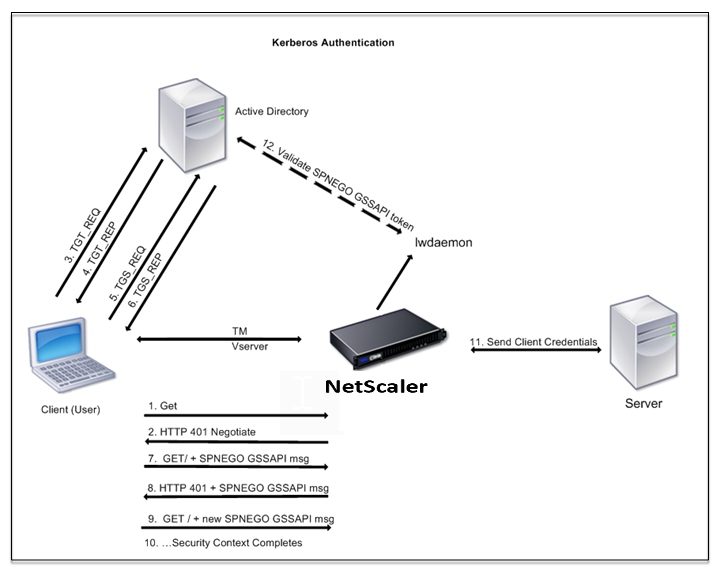
How Citrix Adc Implements Kerberos For Client Authentication

Kerberos Authentication Flow For Browser Based Applications Provided By The As Abap Sap Blogs
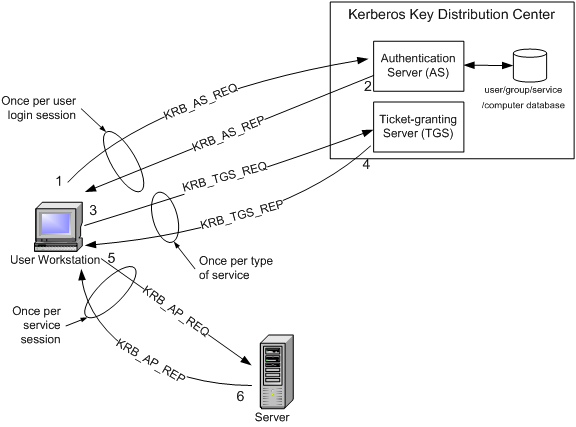
Intel Amt Sdk Implementation And Reference Guide
Request Based Versus Session Based Kerberos Authentication Or The Authpersistnonntlm Parameter Microsoft Tech Community
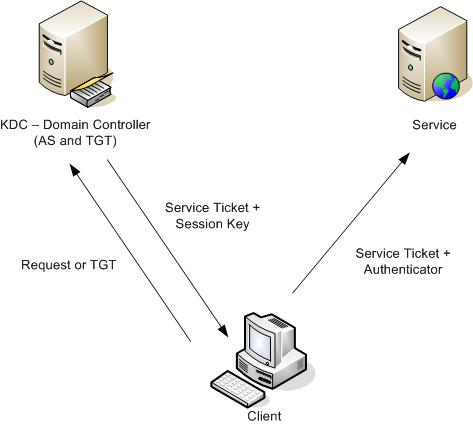
Kerberos Szenarios Data Warehousing Bissantz Company

Understanding Kerberos Concepts Ig Ldap Sso Auth 3 4 0 Documentation

Taming The Beast Kerberos For The Sql Server Dba Youtube
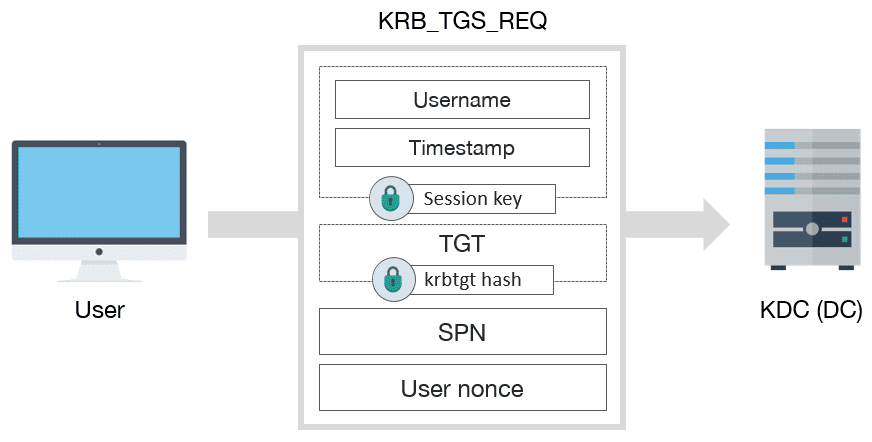
Kerberos I How Does Kerberos Work Theory

Windows Event Id 4768 A Kerberos Authentication Ticket Was Requested Adaudit Plus
Tickets Tokens And Authentication An Introduction To Kerberos Appway Community

Wie Funktioniert Die Kerberos Authentifizierung

1 A Simplified Version Of The Kerberos Authentication System Both The Download Scientific Diagram

Kerberos Authentication Axway Open Documentation
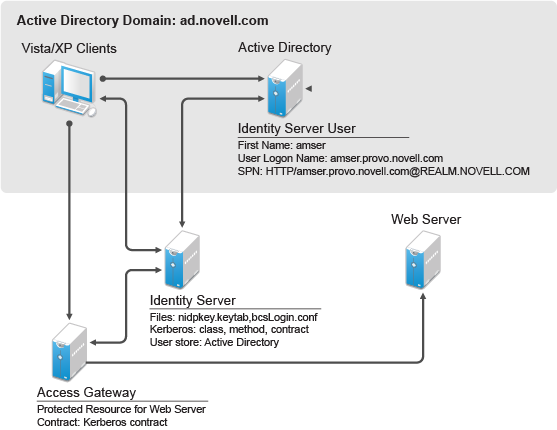
Kerberos Authentication Access Manager 4 5 Administration Guide


